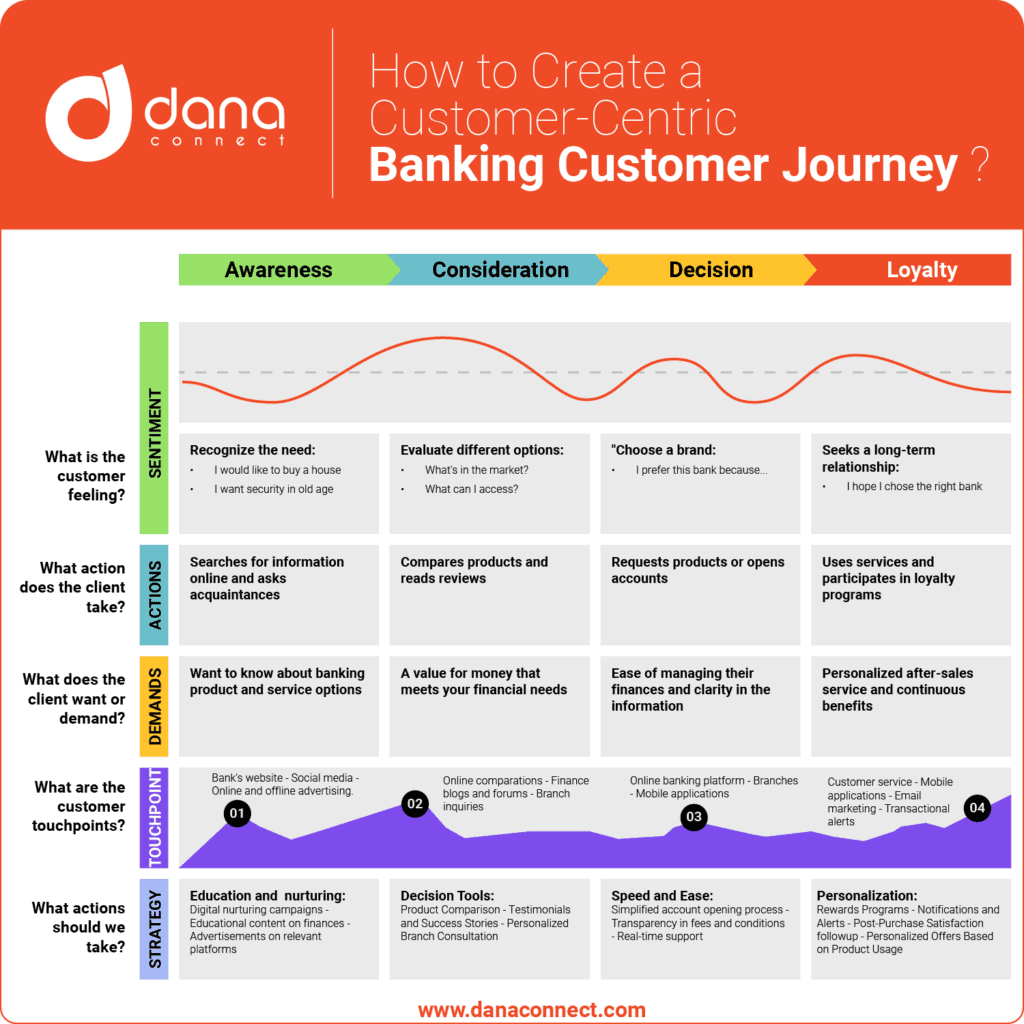
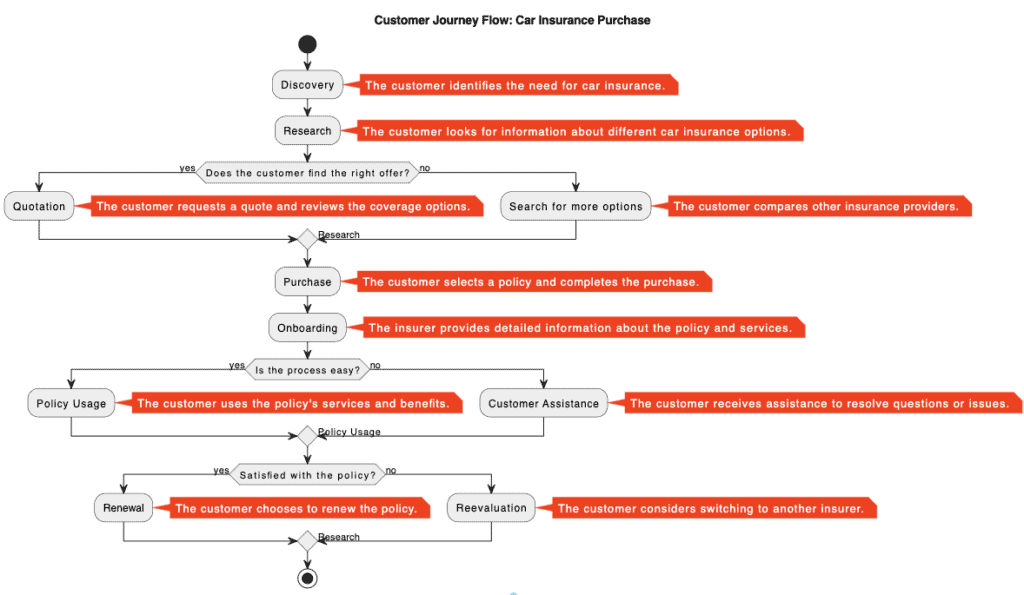
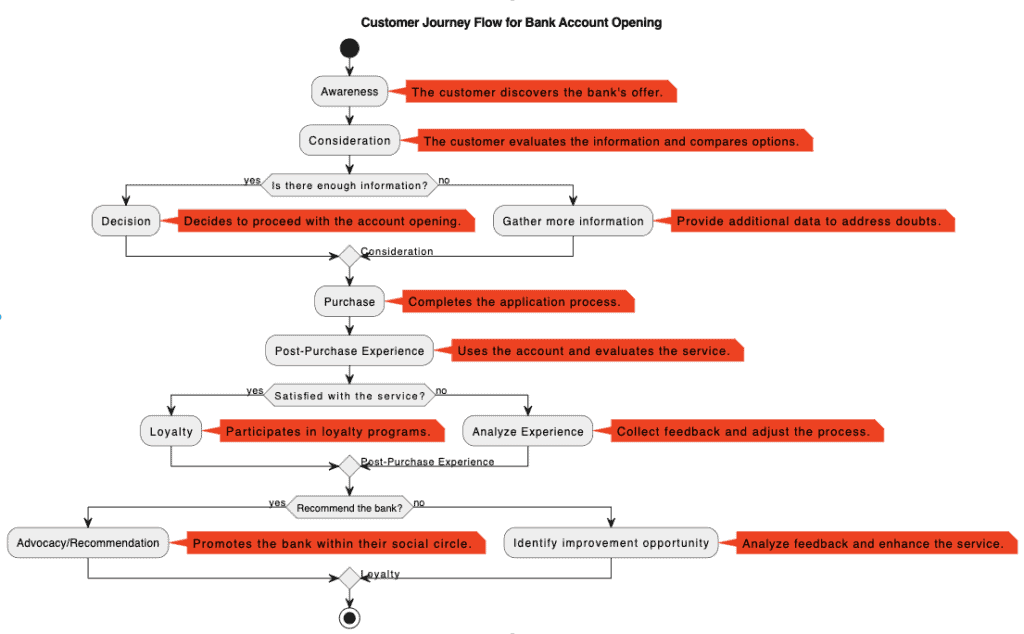
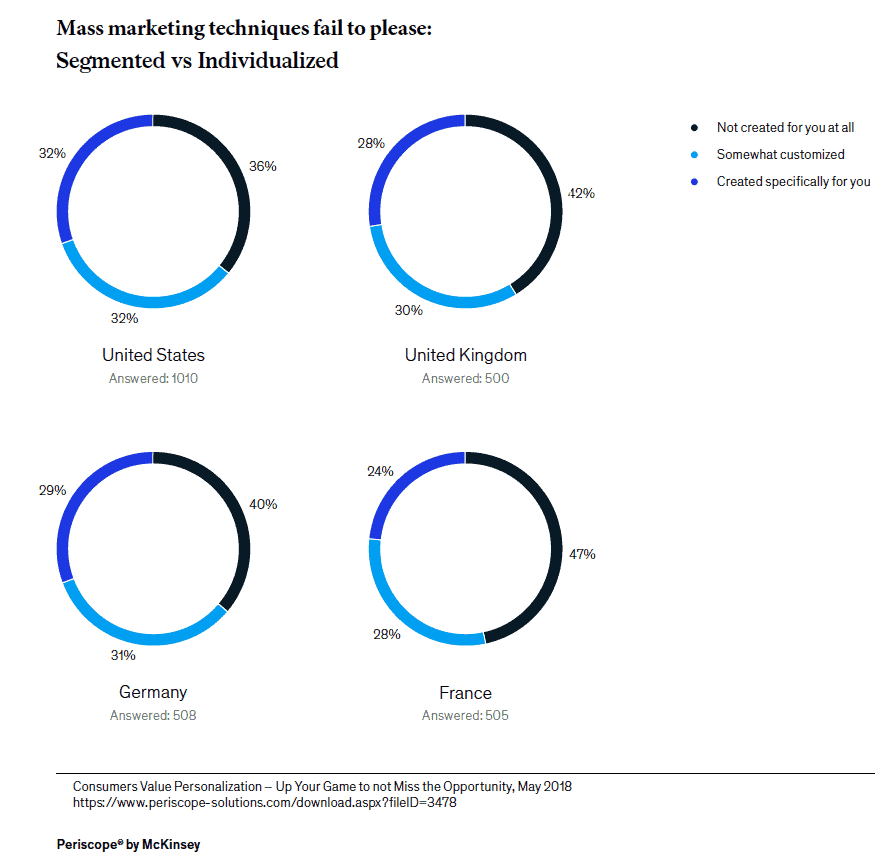
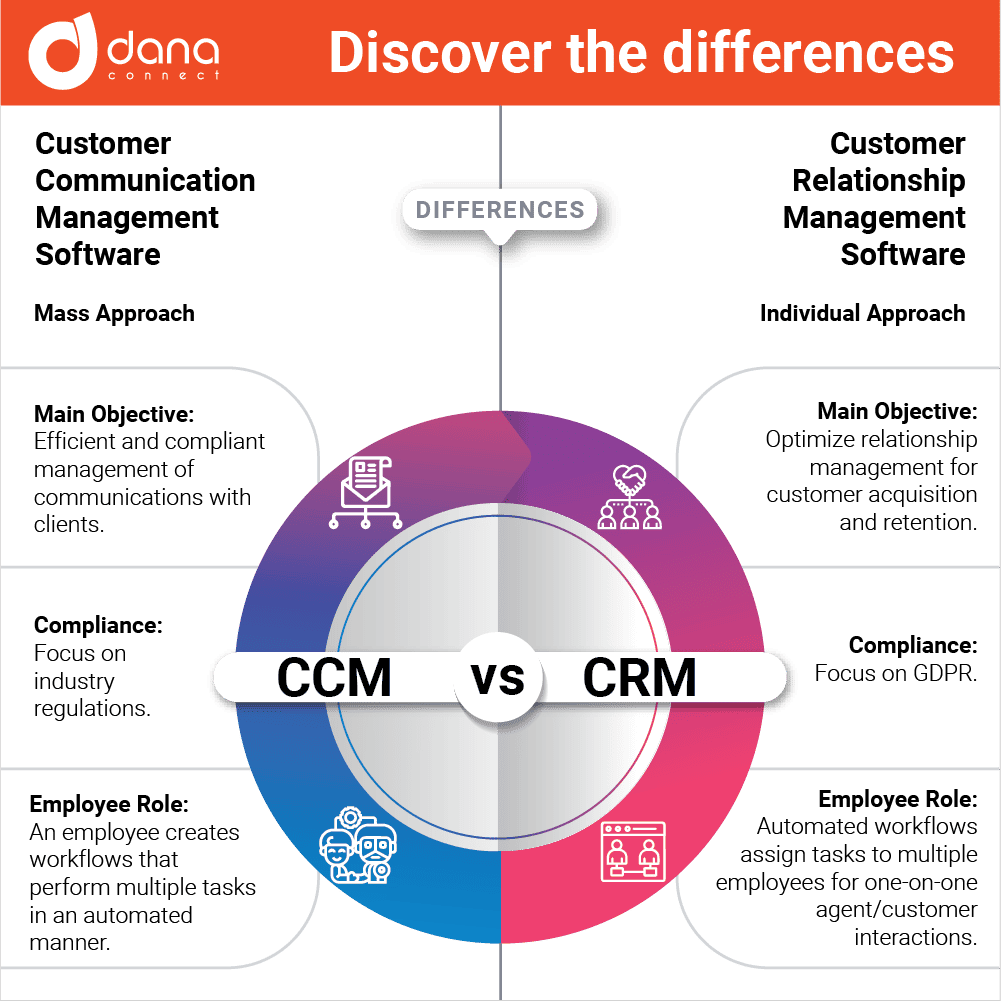
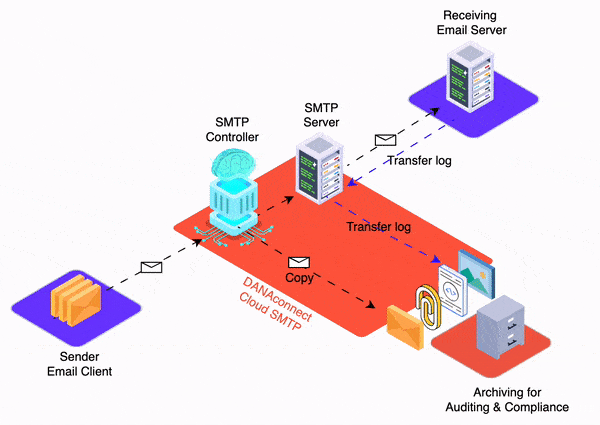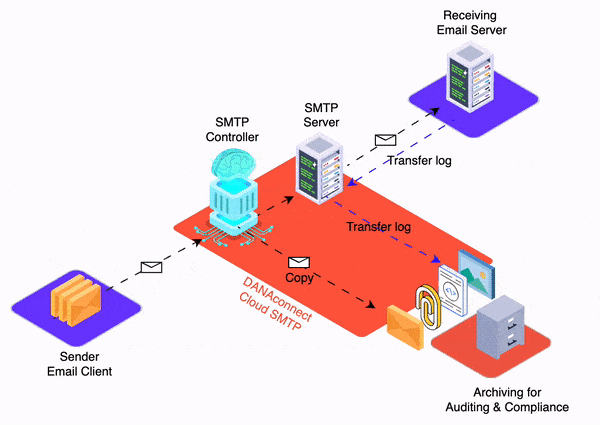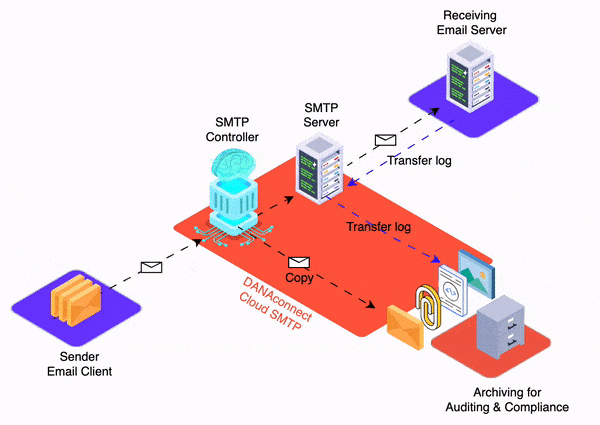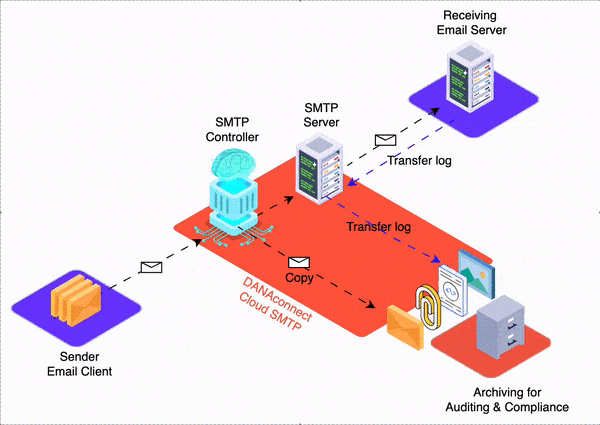
In this article we will discuss how we have successfully applied our “dmarc – relaxed – to – dmarc – strict” step-by-step methodology to various financial clients, including regional banks and local credit unions.
Protection against phishing and identity theft is essential in any organization. In particular, companies that handle financial or personal information must ensure that malicious third parties do not spoof emails sent from their domains.
DMARC (Domain-based Message Authentication, Reporting, and Conformance) is a technical standard designed to help prevent email spoofing. Proper implementation can significantly reduce the volume of spam sent with fraudulent addresses while increasing the SMTP server’s ability to identify and block suspicious messages before they arrive at the inbox.
Update as of January 2024:
This article is from April 2023, however, since February 2024, DMARC implementation has become a requirement by Google and Yahoo for receiving emails in their servers.
Introduction to DMARC
The DMARC protocol acts as an additional protective shield over other antispam technologies (such as SPF – Sender Policy Framework – or DKIM – DomainKeys Identified Mail). It establishes unambiguous rules about what servers can send emails using our name/domain/commercial name, thus making it easier to detect malicious attempts by cybercriminals.
Many companies are afraid to adopt it because they mistakenly believe two myths:
1.- If they activate it, all my emails will be marked as spam, and clients will not be able to receive emails from my brand.
2.- Its implementation is very complex.
The correct adoption of DMARC improves email deliverability and significantly reduces the chances of a bad actor impersonating your email communications. That is, once correctly adopted, deliverability will increase by reducing the volume of existing fraudulent emails (and thus avoiding blocking or deletion).
Other companies implement DMARC and encounter serious problems due to:
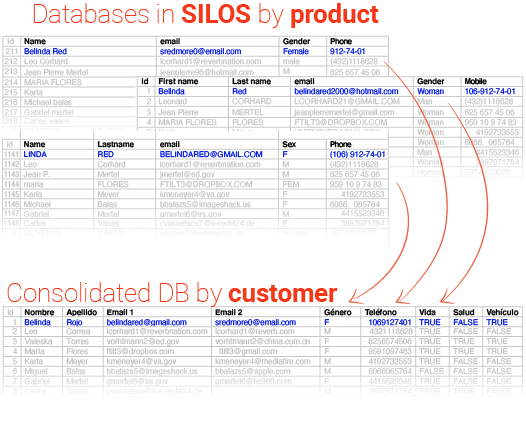
Not having a comprehensive inventory of servers that send emails. This digital asset inventory should include all kinds of sources, which in many cases handle critical processes. From A2P sending servers, scanners with email sending capabilities, external providers such as those who send invoices or documents on behalf of your company, external point-of-sale providers, SaaS that a department has set up from the shadows… the list can be endless.
Step by step to implement DMARC progressively without losing deliverability
Step 1: Check your current policies
First, we must review our current DNS configuration to ensure that SPF is active along with DKIM. If these two protocols have not yet been implemented you will first need to do so before proceeding with DMARC.
SPF validates who can send messages from our domain based on specific records created within the DNS record for that domain; meanwhile DKIM uses asymmetric cryptography to verify if the messages received are originally authenticated by the person who claims to have sent them (this makes it possible to detect phishing attempts). You may find this other article interesting Why is SPF important for email security?
Once this information is verified, we will then proceed to create new additional TXT records necessary to enable DMARC. This step includes adding simple rules where we will indicate actions about what should happen when someone receives a fraudulent message impersonating us.
Step 2: Implement dmarc-relaxed
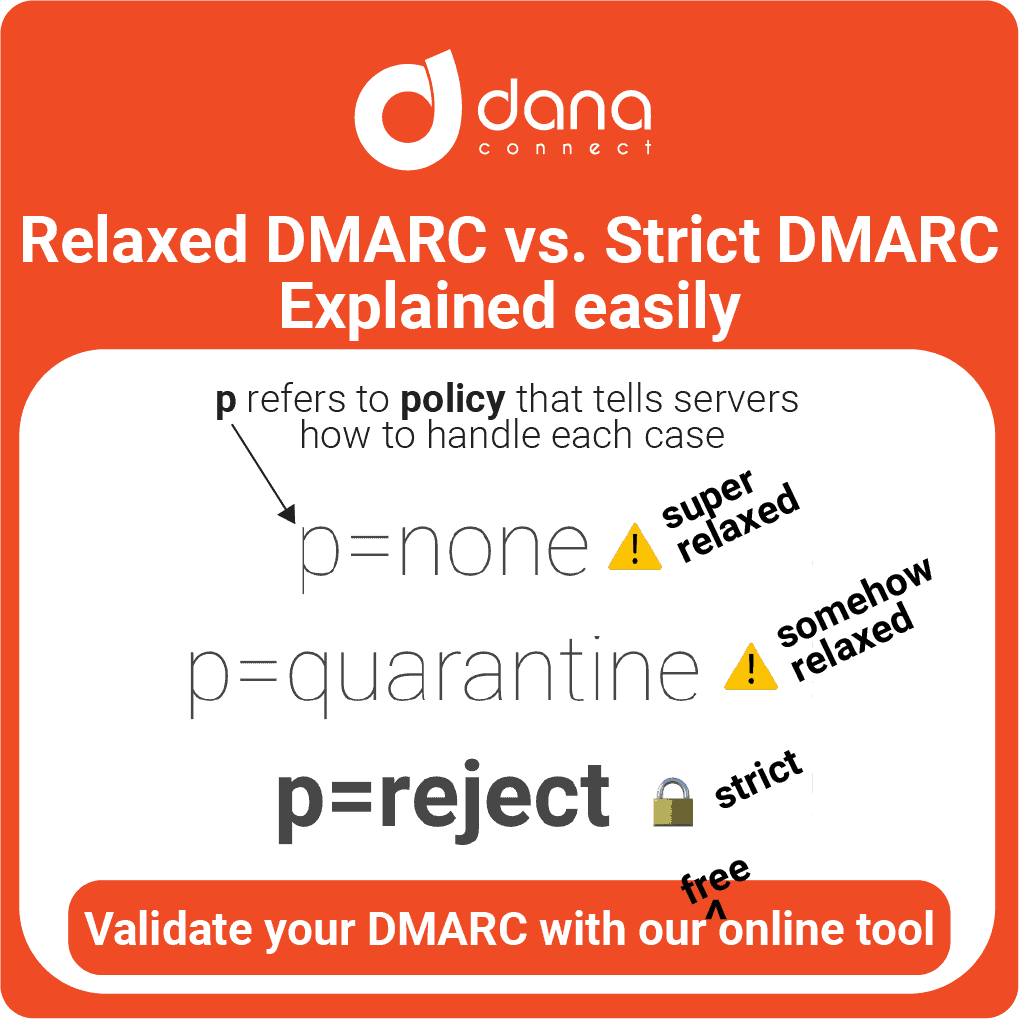
Now we are going to slowly start modifying our rules using “relaxed dmarc”. This first phase will allow us to gradually establish changes without negatively affecting our normal daily processes.
With this mode, we are explicitly telling the recipient’s mail server not to block or reject any fraudulent messages but only to mark them as “failed”. This is useful for analyzing the volume of failed messages and determining which IP addresses are most used by attackers and which are legitimate.
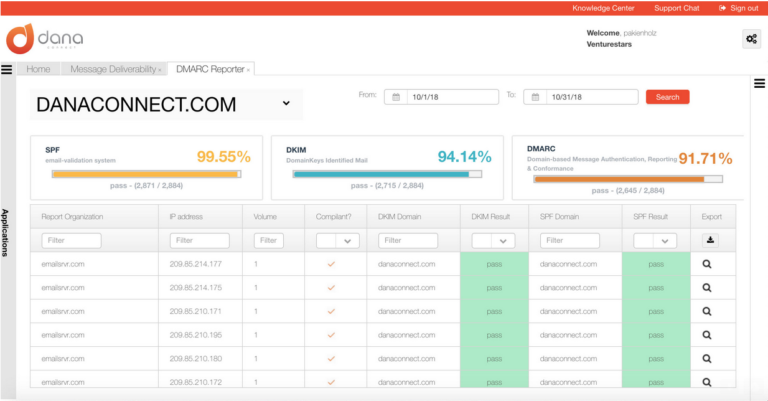
Step 3: Check your reports
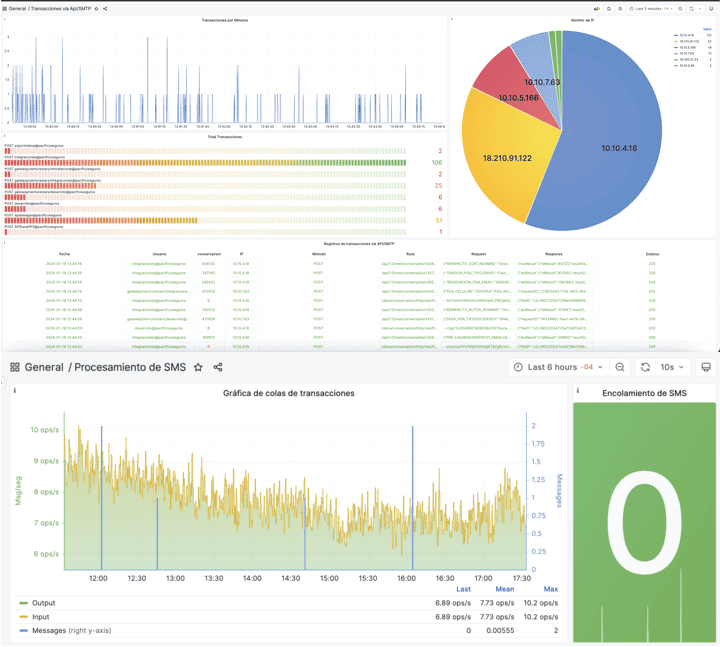
It is time then to check if DMARC reports are being generated. By enabling this option, we can receive daily or weekly reports on how many emails have been sent on our behalf from different sources; so we can see how this changes over time. Learn about the DMARC tool that you can get for free with the DANAconnect platform.
If all went well we should start to see a steady increase in the number of authentic emails (as the number detected as fraudulent decreases). At this point, we already have a clear idea about who is our top legitimate senders and those trying to impersonate us.
Step 4: Implement dmarc-strict gradually
Finally, the time comes, let’s activate DMARC strictly blocking all suspicious messages automatically, marking them as “fail” as well as any email sent without explicit authorization will be directly discarded.
However, we must do it little by little, fine-tuning our rules before we become too restrictive. Otherwise we could negatively affect some critical or mandatory processing but still unknown to us.
Start by setting less aggressive policies first while carefully watching your incoming/outgoing traffic for a while until you are sure. You will probably have to iterate several times between step 3 and step 4.
Conclusion
DMARC implementation is a critical task in protecting against phishing and spoofing. Its adoption, however, must be gradual and careful to avoid negatively affecting normal daily processes.
Our “dmarc-relaxed-to-dmrac-strict” methodology has proven effective for financial clients by significantly reducing the volume of spam sent with fraudulent addresses while increasing our SMTP server’s ability to identify and block suspicious messages before they even reach the recipient ( not even to the spam tray).
This article will be a good starting point for continuous improvement on how you can improve your email security practices from relaxed DMARC to step-by-step progressive strict DMARC.