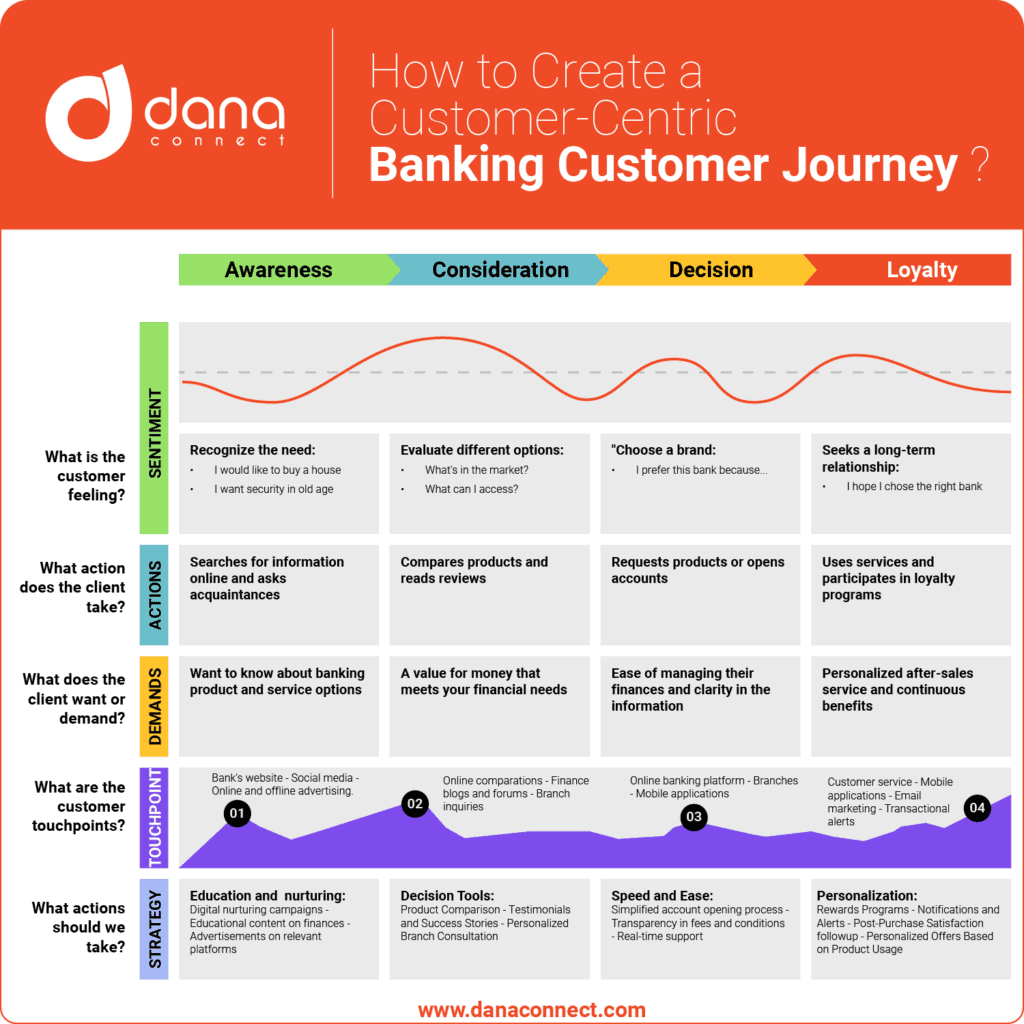
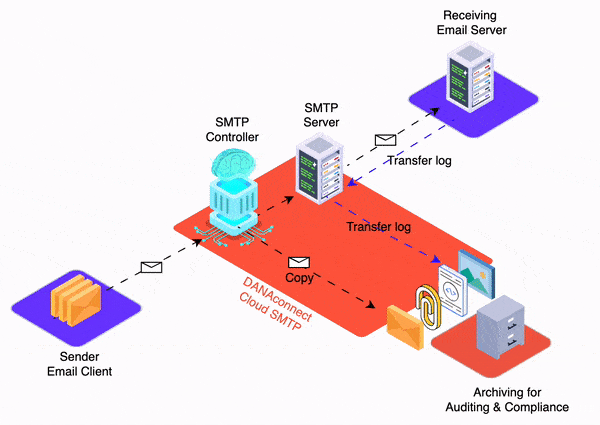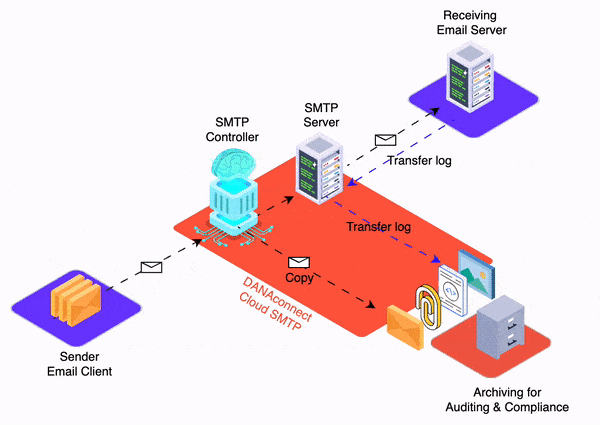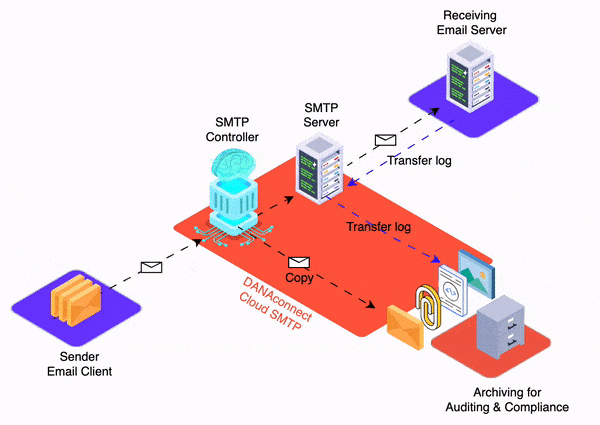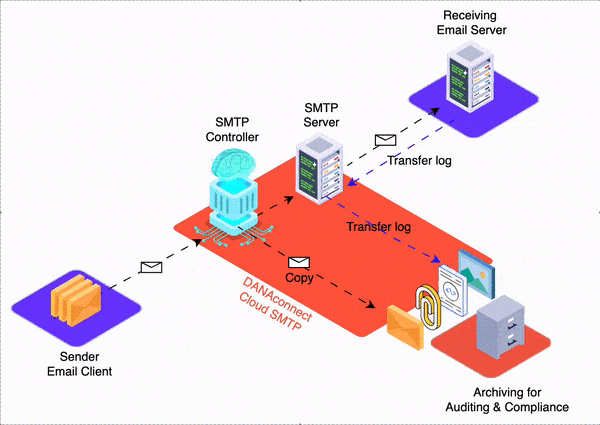
Understanding that 91% of cyberattacks start through the email channel, companies are on the front line of protecting against emerging threats. Starting in April 2024, domains without a valid DMARC record will face another significant challenge: the inability to send email to platforms like Gmail and Yahoo. This underscores not only the importance of adopting DMARC but also the need to adhere to basic security standards to ensure email integrity and deliverability. Differentiating relaxed DMARC versus strict DMARC, through a progressive methodology, becomes a critical step for organizations seeking to strengthen their digital defenses without compromising essential communication with customers and partners. This approach allows businesses to move from a monitoring setup to adopting stricter policies, ensuring a smooth and secure transition to greater email security.
The Need for DMARC
Email is not only an essential communication tool but also a primary vector for cyber attacks. DMARC is a standard that helps protect email domains from abuse by providing a framework for email providers to verify that messages are actually coming from the domain they claim to represent. However, directly implementing strict DMARC policies can lead to legitimate email deliverability issues, impacting business operations and customer communication.
Relaxed DMARC versus Strict DMARC
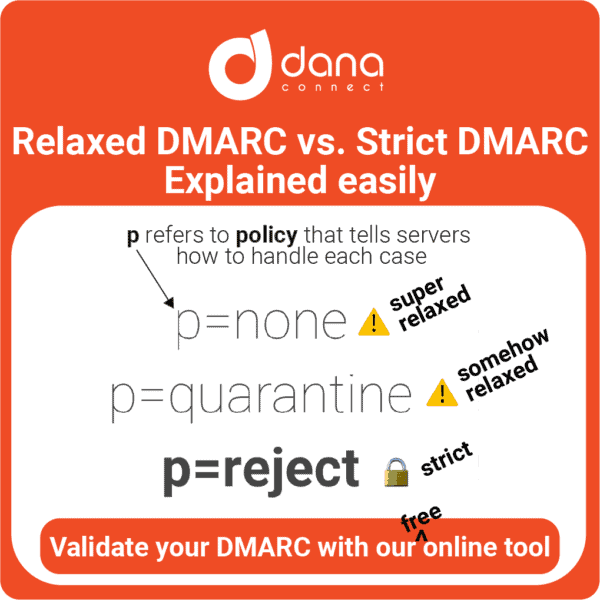
Implementing DMARC is presented as a crucial solution to protect email domains from abuse. However, the choice between a relaxed DMARC approach (p=none) and a strict one (p=reject) is critical, as each has significant implications for email security and deliverability. While relaxed DMARC allows organizations to monitor and adjust their policies without directly impacting the reception of legitimate emails, strict DMARC offers superior protection against phishing and spoofing attacks by rejecting fraudulent emails. The transition from a relaxed to a strict approach should be gradual, allowing companies to identify and resolve problems without compromising communication with their users.
- DMARC Relaxed (p=none): This policy indicates that this domain is monitoring email traffic, but does NOT instruct the receiving server to take any action on emails that fail DMARC verification. It is a reporting mode that does not comply with basic email protection and security standards.
- DMARC Strict (p=reject):This policy instructs receiving servers to reject emails that fail DMARC verification. This is the strictest setting and helps prevent email abuse, minimizing the risk of phishing.
- DMARC Quarantine:This policy, somewhere between relaxed and strict, instructs receiving servers that emails that fail DMARC verification should be quarantined (for example, moved to the spam folder). This reduces the risk of phishing somewhat, but still allows for some failed email delivery.
- If you have lost deliverability when trying to implement DMARC: We recommend that you consider using a tool DMARC Reports.
Progressive Methodology: A Staged Approach
The adoption of DMARC should be a thoughtful and progressive process. Starting with a monitoring-only configuration (p=none), organizations can collect essential data on the performance of their emails without impacting their deliverability. This approach allows you to identify and rectify problems with the SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) configuration before moving towards more restrictive policies such as quarantine (p=quarantine) and finally reject (p=reject).
- Start with SPF and DKIM: The foundation of a successful implementation begins with the correct configuration of SPF and DKIM, ensuring that emails sent on behalf of the domain are properly authorized and signed.
- Monitor (p=none): Enabling DMARC in monitoring mode is crucial to understanding email flow and identifying legitimate and illegitimate email sources, without interfering with deliverability.
- Gathering information: A critical step is to identify all legitimate email services used by the organization, ensuring they are recognized and authorized in future DMARC policies.
- SPF and DKIM Reconfiguration: Based on the information collected, SPF and DKIM settings are adjusted to accurately reflect authorized email sources.
- Transition to Quarantine (p=quarantine): Moving emails that fail DMARC verification directly to the spam folder reduces the risk of phishing, while allowing for additional adjustments based on the observed results.
- Final Settings and Strict Mode (p=reject): The final step is to adopt a rejection policy, where emails that fail DMARC verification are blocked completely, maximizing email security.
Risks of an Accelerated Strict DMARC Implementation
Skipping stages in this progressive methodology can have significant consequences. Legitimate emails could be marked as spam or rejected, disrupting essential communication with customers and partners. Accurate inventory of email providers and careful implementation of DMARC policies minimize these risks, ensuring a smooth transition to improved email security.
An Advanced Level of Configuration: What are the parts of a DMARC Record?
| Tag | Tag Value | What does it indicate? | Description |
|---|---|---|---|
| v | DMARC1 | Version | Indicates the DMARC protocol version in use. |
| p | none, quarantine, reject | Policy | Defines the policy to be applied to email that fails the DMARC check. |
| sp | none, quarantine, reject | Subdomain Policy | Defines the policy for subdomains, which can be different from the main domain policy. |
| pct | 1 to 100 | Percentage | Specifies the percentage of messages subjected to filtering that will apply the DMARC policy. |
| rua | mailto:admin@example.com | Aggregate Reports | Specifies a URI to send aggregate reports of DMARC failures. |
| ruf | mailto:admin@example.com | Forensic Reports | Specifies a URI to send forensic reports of individual message failures. |
| adkim | r, s | DKIM Alignment Mode | Specifies strict or relaxed DKIM identifier alignment. |
| aspf | r, s | SPF Alignment Mode | Specifies strict or relaxed SPF identifier alignment. |
| fo | 0, 1, d, s | Failure Reporting Options | Specifies the conditions under which the reporting organization sends failure reports. |
| rf | afrf, iodef | Report Format | Specifies the format of the message reporting (afrf or iodef). |
| ri | Integer | Report Interval | Specifies how often you want to receive the aggregate reports in seconds. |
An Advanced Level of Configuration: Alignment of adkim and aspf Policies
In the introduction to the topic of DMARC and email security, at a more advanced level we begin to understand the importance of the adkim and aspf tags, components of the DMARC policy that, although not essential to declare, help organizations in a more specialized way to protect their email domains against identity impersonation and other types of phishing attacks.
The adkim tag refers to DKIM alignment, specifying how the domain in the DKIM signature of an email compares with the domain in the “From” field of the message. The options are “r” for relaxed, where domains must be from the same Organizational Domain, and “s” for strict, where domains must match exactly.
The aspf tag refers to SPF alignment, which establishes how the domain used for SPF verification should be compared to the domain in the “From” field of the email. As with adkim, the options are “r” for relaxed and “s” for strict.
Including these tags in an organization’s DMARC policy provides more granular control over how email messages are validated and reinforces domain security, minimizing the risk of abuse and phishing attacks. By specifying these policies, organizations can ensure that only authenticated and verified emails are delivered, while suspicious or fraudulent messages can be rejected or quarantined, according to the organization’s preferences.
The correct implementation of DMARC with appropriate settings for adkim and aspf is the next and more advanced step, after having declared the DMARC policy.
Handling DMARC Authentication Failures
Understanding how to configure and align DKIM and SPF policies is crucial for effectively managing cases where DMARC authentication fails. While DMARC provides an additional layer of verification, its effectiveness depends on careful configuration of these alignments. The DMARC policy will fail if both DKIM and SPF verifications fail in their respective alignment, which could lead to legitimate emails being rejected or marked as spam.
To ensure maximum effectiveness of DMARC and avoid interruptions in email delivery, it is recommended to do the following:
- Continuous review of alignment policies: Ensure that alignment policies for DKIM and SPF are configured to meet your organization’s security requirements, adjusting as necessary.
- Monitoring and adjustment: Use DMARC Reports to monitor the performance of your emails and adjust alignment settings to optimize delivery.
- Education and testing: Train your team on the implications of DKIM and SPF alignment and conduct periodic testing to ensure that the current configuration remains effective against changes in email sending practices.
Conclusion on Relaxed DMARC versus Strict DMARC
Implementing DMARC is not a simple switch that is flipped, but rather a meticulous process that protects an organization’s email communication. Through a progressive methodology, companies can strengthen their digital security without sacrificing email deliverability, ensuring that only authentic messages reach their recipients.