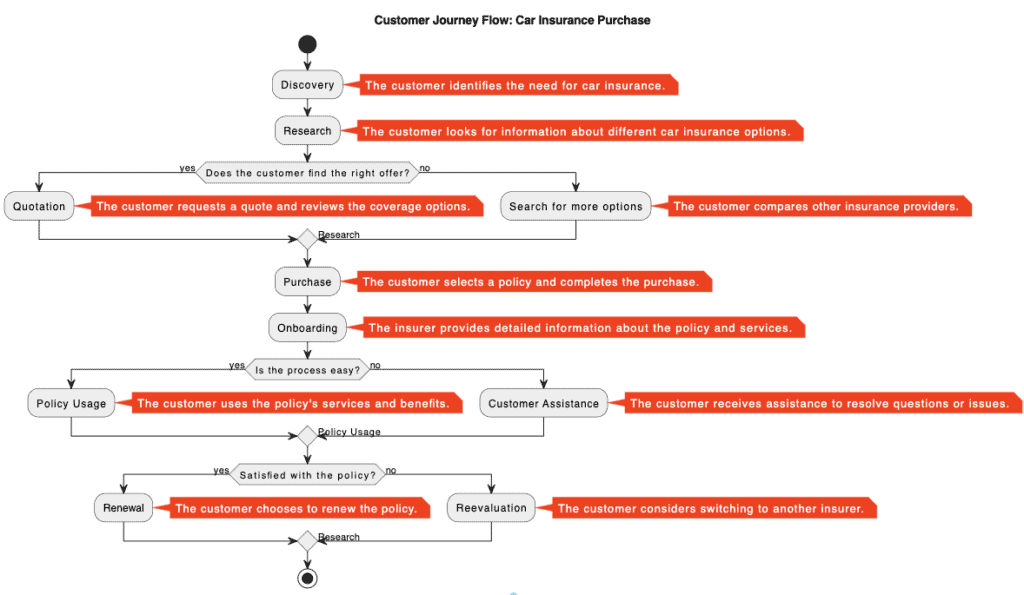
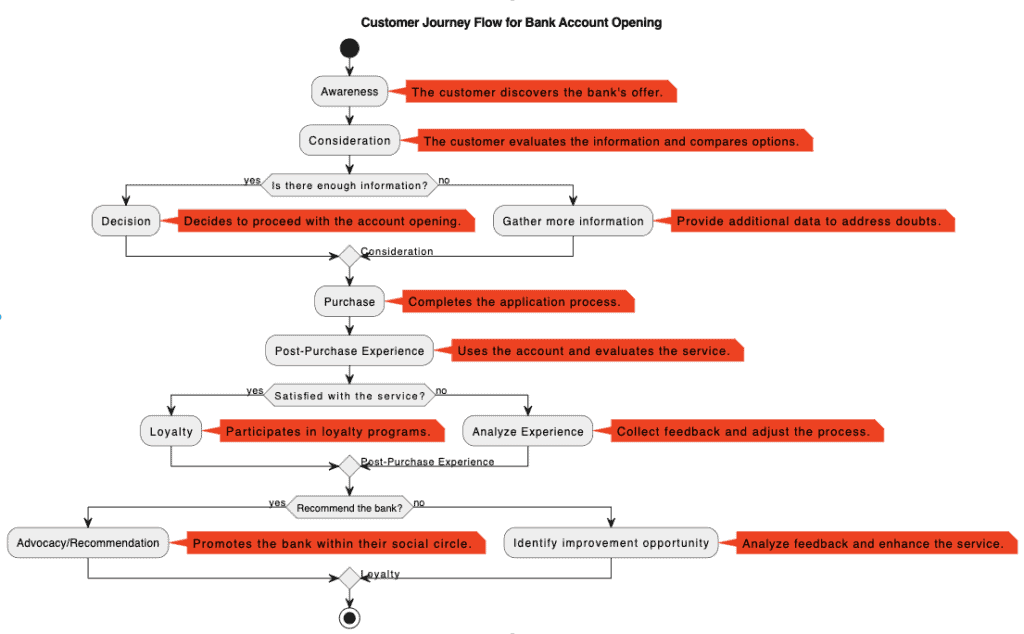
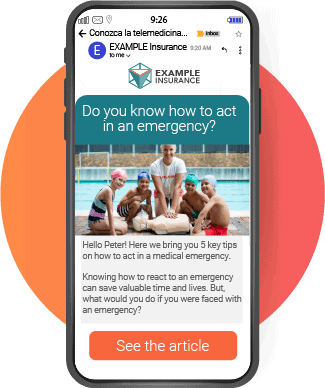
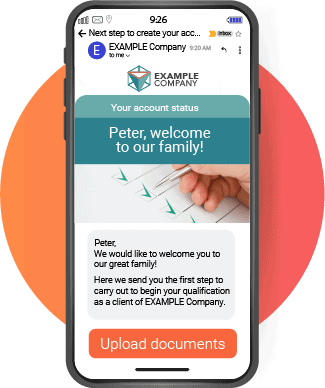
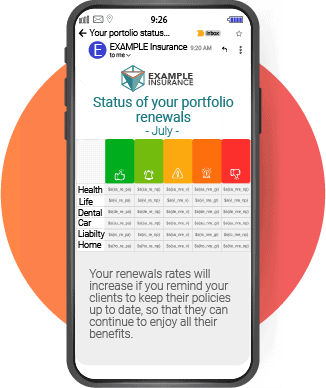
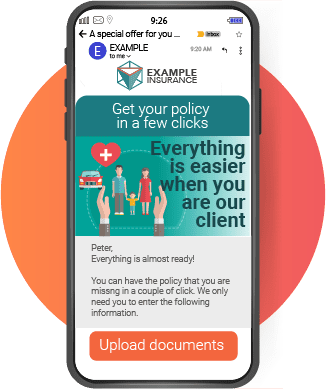
In the current era of cybersecurity, where threats are constantly evolving and traditional perimeters have become obsolete, organizations are challenged to protect their networks and data with more efficient and adaptable strategies. This is where Zero Trust Architecture takes on a leading role, offering a revolutionary approach to computer security. This model, based on the principle of “never trust, always verify”, is especially relevant for financial institutions, where the protection of sensitive information is of utmost importance.
In this article, we explore the ten most important things to know about Zero Trust Architecture, breaking down its meaning, applications, and impact on the security of financial organizations. From multi-factor authentication to micro-segmentation and cloud integration, each point will provide a deeper understanding of how Zero Trust is not just a security policy, but a comprehensive strategy that transforms the way companies protect their digital assets in an interconnected and constantly changing world.
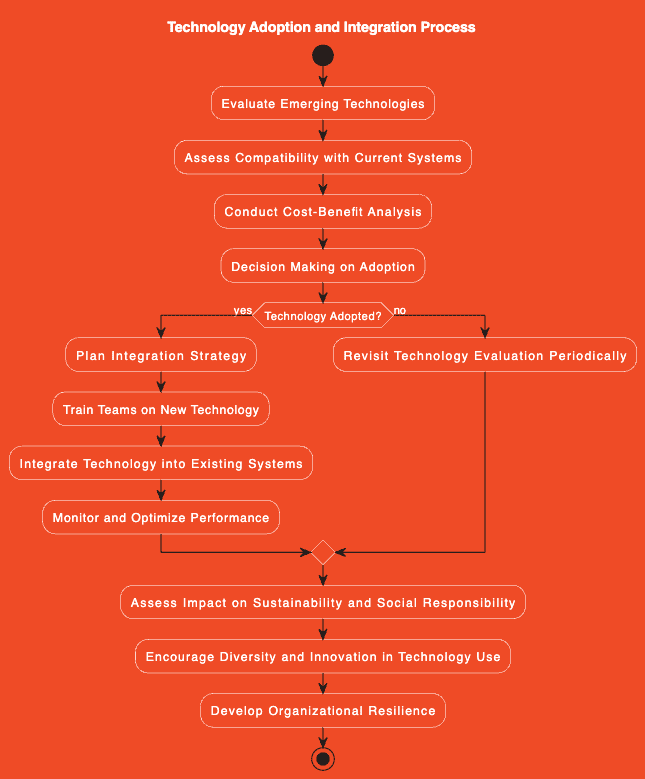
1. Definition of Zero Trust Architecture
Zero Trust It is a computer security model that operates under the principle that no entity inside or outside the network is trusted by default. This model requires rigorous verification of every connection request, regardless of its origin, representing a fundamental shift from traditional security approaches.
2. Principle of “Never Trust, Always Verify”
The core philosophy of Zero Trust is “Never trust, always verify”. This approach implies that all entities, whether internal or external, must be authenticated and authorized before being granted access to network resources. This principle is crucial to minimizing vulnerabilities in today’s digital environment.
3. Importance in the Financial Sector
In the financial sector, where security and data protection are paramount, implementing Zero Trust can be a key differentiator. Financial institutions face growing and sophisticated threats, making a robust and adaptable security model like Zero Trust more relevant than ever.
4. Microsegmentation to Improve Security
Micro-segmentation is an essential component of Zero Trust. It consists of dividing the network into small, controlled zones to limit access and lateral movement of attackers within the network. This technique helps protect sensitive data, even if an attacker manages to penetrate the network.
5. Role-Based Access Control
Another important aspect of Zero Trust is role-based access control. This means that access to information and resources is granted strictly based on need and the user’s role, ensuring that individuals have only the access necessary to perform their functions.
6. Multi-Factor Authentication (MFA)
The Multifactor Authentication is a pillar of Zero Trust. MFA adds additional layers of security by requiring two or more credentials to verify the user’s identity. This can include something the user knows (such as a password), something they have (such as a mobile phone), and something they are (such as fingerprints). MFA is essential to protect against identity and credential theft attacks.
7. Continuous Monitoring and Analysis
Zero Trust is not just a one-time implementation; It is a continuous process. Constant monitoring and analysis of network behavior makes it possible to detect and respond to threats in real time. Using advanced analytics tools and artificial intelligence to evaluate network traffic is critical to maintaining an effective security posture.
8. The Importance of Total Network Visibility
Complete network visibility is crucial in a Zero Trust architecture. This involves having a clear understanding of all devices and users connected to the network, as well as data flows. Complete visibility enables better anomaly detection and faster response to potential threats.
9. Zero Trust and Regulatory Compliance
Regulations in the financial industry, such as GDPR, HIPAA and others, require a high level of data protection. Zero Trust helps organizations comply with these regulations by rigorously managing data access and constant monitoring, which can be crucial to avoiding penalties and maintaining customer trust.
10. Challenges and Considerations for Implementation
Transitioning to a Zero Trust architecture can be challenging, especially for organizations with legacy infrastructures and systems. It is important to do detailed planning, take a step-by-step approach and ensure you have the right support and training for staff. Choosing a trusted technology partner who can guide and support this process is essential.
To go…
To conclude, Zero Trust Architectures represent a fundamental and necessary change in the way organizations, especially in the financial sector, approach cybersecurity. This model not only improves protection against external and internal threats, but also fosters a more aware and robust security culture.
Implementing Zero Trust requires a comprehensive approach, ranging from multi-factor authentication and micro-segmentation, to integration with emerging technologies and user experience management. Although the transition may present challenges, especially in organizations with complex infrastructures and legacy systems, the benefits in terms of improved security, regulatory compliance, and cyber resilience are clear and significant.
Ultimately, adopting Zero Trust is not just a technical decision, but a business strategy that responds to the increasing sophistication of cyber threats in an increasingly digitalized and connected world. Organizations that proactively adopt this model will be better equipped to protect their critical assets, maintain the trust of their customers and partners, and secure their future in the dynamic cybersecurity landscape.