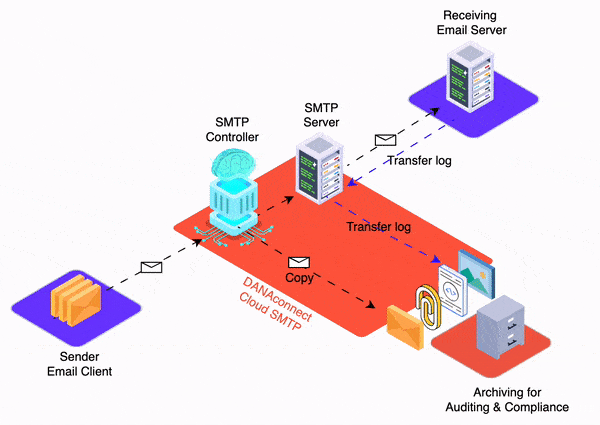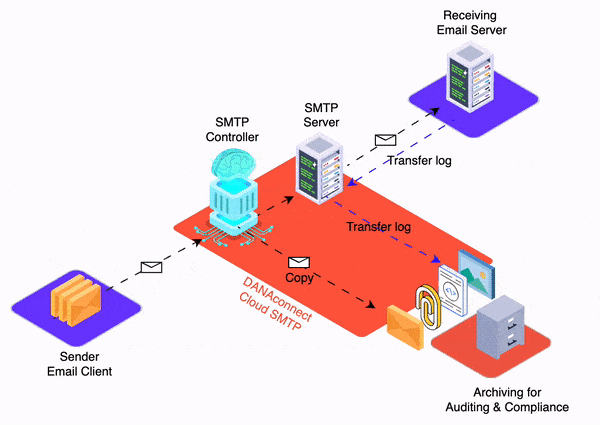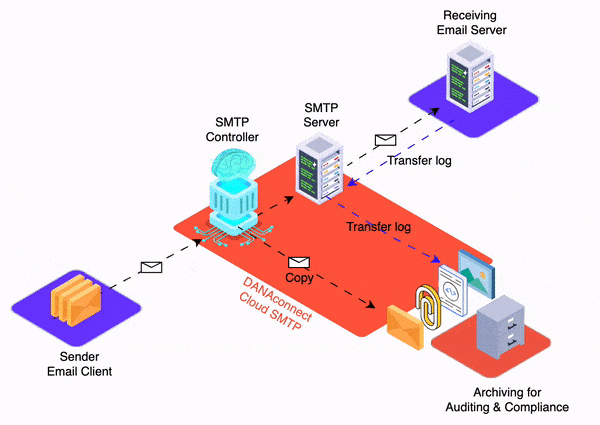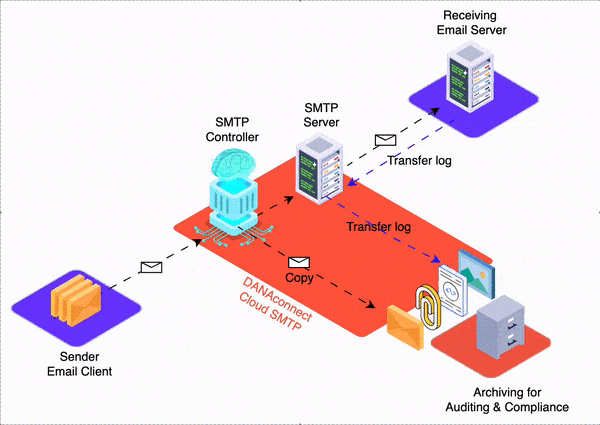
In an environment where dependence on email as a means of corporate communication remains high, the security and authenticity of each message are essential to protect information and maintain trust in digital interactions. The DKIM (DomainKeys Identified Mail) Digital Signature is an email authentication technique that allows an organization to take responsibility for sending a message in a verifiable manner. This directly contributes to the fight against phishing and email fraud, which over time have proven to be persistent security problems for businesses of all sizes.
The Need for the DKIM Digital Signature in Corporate Communication
Attackers frequently use spoofing techniques (spoofing) to send emails that appear to come from legitimate sources within a company. This can lead to security breaches, loss of sensitive data, and damage to brand reputation. DKIM serves as a defense mechanism, assuring recipients that the content of the message has not been altered from its origin and that it truly comes from a specific domain.
What is the DKIM Digital Signature and How Does It Work?
DomainKeys Identified Mail (DKIM) is an email authentication protocol that provides a way to verify that a message was sent and authorized by the domain owner. This is achieved through a message signing and validation system that uses asymmetric cryptography.
When an email is sent from a domain that uses the DKIM digital signature, the sending server generates a unique signature based on the content of the message, which includes a special header and is attached to the email. This digital signature is linked to a DNS record of the sender’s domain, which contains a corresponding public key used for verification.
When the message reaches its destination, the receiving server queries the DKIM DNS record of the sender’s domain to obtain the public key. It then uses this key to decrypt the signature and compare it with one newly calculated from the received message. If both signatures match, it is confirmed that the message has not been tampered with and that it comes from the domain it claims to come from.
How is the DKIM Digital Signature implemented in the Company? Critical Steps for Effective Authentication
1. Key Generation and Integration with DNS
The first step in implementing the DKIM digital signature is the generation of a pair of keys, one private and one public. The private key will be used by the company’s email system to sign outgoing messages. The public key, on the other hand, is published to the domain’s DNS as a TXT record, allowing receiving servers to use it to validate incoming messages.
2. Mail System Configuration
The next step is to configure the email system to use the generated private key to automatically sign all outgoing messages with a DKIM signature. This is typically done on the outgoing mail server (MTA), or through an email security solution that offers DKIM support.
3. Security Policy and Practices
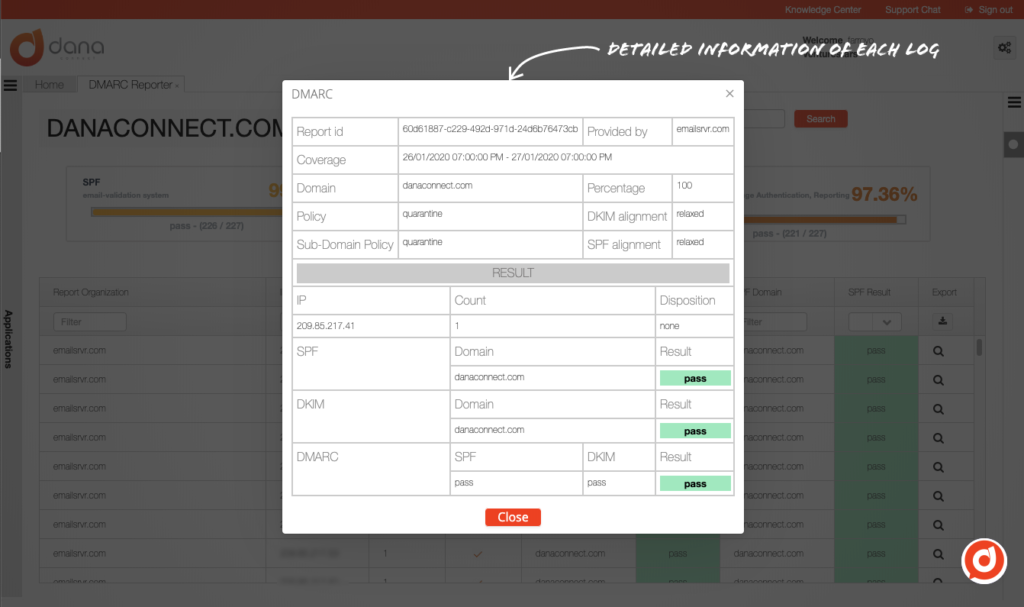
Implementing a protocol like DKIM also requires a robust security policy that covers key management and key renewal frequency, as well as additional email security measures such as SPF (Sender Policy Framework) y DMARC (Domain-based Message Authentication, Reporting & Conformance).
Advantages of DKIM for Companies
Implementing DKIM comes with a number of tangible benefits for organizations:
- Improved email deliverability: Email servers that make use of DKIM typically have higher deliverability rates, as spam filters consider authenticated messages to be less likely to be spam.
- Brand and reputation protection: By assuring recipients that messages are genuine and have not been altered, companies protect their integrity and maintain trust in their digital communication.
- Preventing phishing attacks: DKIM makes it difficult for attackers to send fraudulent emails that appear to come from the company, which in turn helps protect customers and employees from being fooled by phishing attempts.
- Compatibility and scalability: DKIM requires no changes to email infrastructure and can be implemented alongside other email authentication standards for additional protection.
Conclusion: Strengthening Trust in Business Communication with DKIM, SPF and DMARC
The implementation of security measures such as the DKIM Digital Signature in a company’s email infrastructure is not only an investment in technology but also a commitment to reliability and corporate reputation. In the constant game of cat and mouse that characterizes cybersecurity, organizations that take control and proactively authenticate their communications take a step forward in building secure digital relationships and protecting their assets.
An implementation together with SPF and DMARC results in a comprehensive strategy that protects organizations against email abuse and phishing attacks. While DKIM ensures that email content is kept intact from its origin, SPF validates that emails are sent by authorized servers, and DMARC brings the two checks together to provide a clear policy on how emails that fail verification should be handled. authenticity checks.
The collaboration between DKIM, SPF and DMARC It forms a defensive triumvirate that not only reduces the risk of being another victim in the world of cybercrime, but also increases the trust of customers and partners by ensuring authentic communication. However, technology is only part of the equation. Effective implementation of these tools depends on ongoing training and commitment to security practices by all employees of a company.
As we navigate an increasingly digital future, diligence in implementing email security solutions like DKIM, SPF and DMARC becomes increasingly critical. It is these proactive measures and continued user education that will enable businesses to maintain the security and integrity of their business communication in cyberspace.